Ransomware is a constantly evolving global threat in the cyber security landscape. The number of ransomware attacks reported globally had jumped in folds. Like wise, in Singapore, the number of ransomware cases reported to CSA also increased. Some of the high profile cases include:
- French insurer Axa hit by cyberattack in Asia (https://www.channelnewsasia.com/news/business/french-insurer-axa-hit-by-cyberattack-in-asia-14824584)
- JBS attack points to food industry cyber weaknesses (https://www.straitstimes.com/tech/tech-news/jbs-attack-points-to-food-industry-cyber-weaknesses-singapore-vulnerable-too)
On 17 June 2021, CSA (Cyber Security Agency of Singapore) published an article “Ransomware: A Growing Cybersecurity Threat to Businesses” to advise companies on the growing danger of ransomware and shared some preventive measures to take against Ransomware.
What is Ransomware?
Ransomware is malware designed to deny a user or company access to files on their computers. It encrypt the files and demanding a ransom payment for the decryption key.
How does Ransomware spread?
The most common method is through phishing emails that contains malicious link to a website hosting a malicious download or an attachment that has downloader functionality built in. If the email recipient falls for the phish, then the ransomware is downloaded and executed on their computer.
Once ransomware has infected a computer, it begin encrypting the computer files. Some types of ransomware may propagate across the network by exploiting vulnerabilities in background services and infect other systems. Once file encryption is complete, the ransomware make a ransom demand.
Ransomware attacks are disruptive to business operations as the infected files will be inaccessible. It is difficult to recover infected files as each type of ransomware requires a unique decryptor, which may not be available for newer ransomware variants.
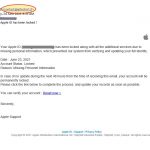
The above example is supposed to be an email from Apple Support. A look at the domain shows “gitechsrl.it” which is unrelated to Apple. This is deceptive and should not be clicked.
Be wary of emails that come from an unrecognized sender or are impersonalized and avoid emails that ask you to confirm personal or financial information. You should check the sender’s email address and verify if the email is legitimate. This should mitigate your chances of falling victim to such email phishing scams.
In the article published on 26 Jun 2021 “It doesn’t pay to pay ransom to hackers: Study“, the author highlighted that a recent study has found that even if a company pays the ransom hackers demand to release files locked up in a ransomware attack, the hackers can still strike again. It also mentioned that CSA indicated that paying them “also encourages the threat actors to continue their criminal activities and target more victims. Threat actors may also see organisations that have paid up as a soft target and may strike again in the future.”
CSA said it is instead focused on helping companies and providing them with advice on how to take preventive measures. “Prevention is key to avoid falling victim to ransomware,” it said.
We fully agree with CSA’s advice.
As a clinic management software provider, we have the responsibility to provide a secured platform that helps prevent, detect, and respond to possible threats.
Our platform is designed with integrated security monitoring and policy management across it.
-
- Multi-layer design
- Internal security policies and procedures
- Antimalware
- Regular security updates
- Backup & Recovery
- Conduct penetration test and vulnerability
- Dedicated personnel for handling hardware security and monitoring of abnormal activity in server
- Two factor authentication for front facing and backend
If your clinic system still resides in your clinic, did you implement any security measures? If you did, is it sufficient?
If you are currently using a clinic system, does it provide sufficient protection to your clinic data?
We take serious approach towards data security and built a secure platform that protects our clients’ data.
Do not leave it to chances. Contact us to find out how our platform can assist you to protect your clinic data from these threats.
Phone: (65) 8180 4207
Email: enquiry@eclinic.com.sg